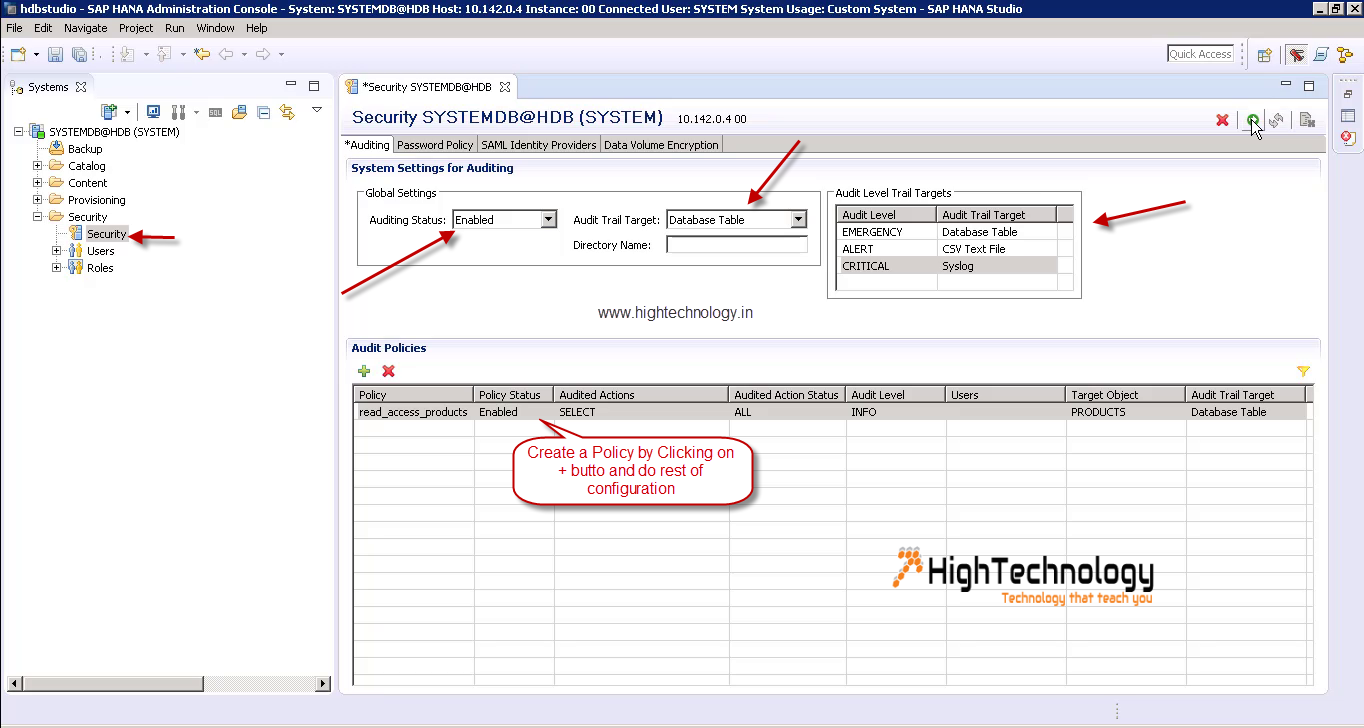
Hi SAP enthusiasts,
SAP Transaction Code SM20N (Analysis of Security Audit Log) - SAP TCodes - The Best Online SAP Transaction Code Analytics. The Security Audit Log is a tool designed for auditors who need to take a detailed look at what occurs in the SAP System. By activating the audit log, you keep a record of those activities you consider relevant for auditing. You can then access this information for evaluation in the form of an audit analysis report. The table below lists the kernel parameters. You can set these parameters as profile parameters in the application server's instance profile, but we recommend you set the parameters dynamically as kernel parameters in the security audit log configuration (transaction SM19 in the Kernel Parameters tab). Once set, the system ignores the profile parameters in the profile of the application. Enable audit logs. The following steps show you how to enable Data Access audit logs: In the main table on the Audit Logs page, select one or more Google Cloud services from the Title column.
the Security Audit Log [SAL] contains information about important system events and should, therefore, better not get lost unintentionally!
Let's see, how the Audit Log can be erased and what we can do to prevent this and maximize its protection.
The Audit Log is stored in log-files that are located in the file system (see parameter DIR_AUDIT) and is either rotated daily or when the current file is full (see parameter rsau/max_diskspace/per_file).
Sap Hr Audit Log Table
Access to these files is possible via kernel functionality (from within the SAP system) or on operating system level (e.g. via an external OS command). We'll focus on access via the SAP application server and won't take a deeper look at manipulations directly from OS level (i.e. from the command line).

The Audit Log is stored in log-files that are located in the file system (see parameter DIR_AUDIT) and is either rotated daily or when the current file is full (see parameter rsau/max_diskspace/per_file).
Sap Hr Audit Log Table
Access to these files is possible via kernel functionality (from within the SAP system) or on operating system level (e.g. via an external OS command). We'll focus on access via the SAP application server and won't take a deeper look at manipulations directly from OS level (i.e. from the command line).
Ways to delete the Security Audit Log
X2 hot pro driver adjustments utility. From inside the SAP system, three variants of deleting the SAL files exist.
Below we'll check them and see, which measures exist to protect the logs. Young jeezy recession album free download.
Variant 1: SM18 (or function module RSAU_CLEAR_AUDIT_LOG or system function C_REMOVE)
SM18 is the SAP standard way of removing old SAL files.
The transaction is protected by an authorization check for S_ADMI_FCD with value AUDA (= AUDit log Administration). The minimum age of files to be erased is 3 days − a nice feature because an attacker cannot remove fresh logs and hide what he/she did moments ago.
Sap Sm20 Audit Log Table
Protection
SM18 is not really problematic… S_ADMI_FCD with value AUDA is a critical authorization, which nobody should be assigned to on production.
Sap Audit Log Table 2020
Diving a bit deeper…
A clever developer might try to copy the code that is responsible for the deletion to a customer report − fortunately, this does not work… see below:
